By Bernhard, editor of Moon of Alabama
ProtonMail is a Swiss provider of an end-to-end encrypted email application. The service is free to use for consumers but sold to businesses and other organizations.
ProtonMail claims to have "Swiss Privacy Data Security and Neutrality".

But how far can one trust ProtonMail's claims of a secure service when it is openly breaking, as we show below, its pledge of neutrality?
During the aftermath of the emergency landing in Minsk of a Ryanair flight between Greece and Lithuania ProtonMail provided fractional information about emails which delivered a bomb threat against the plane to several airports. The partial and seemingly willfully incomplete response by ProtonMail has led to false claims by various media against the government of Belarus.
The 'west' is currently waging an information war against Belarus. It wants to change the government of Belarus by whatever means. By only providing fractional information about the case ProtonMail has taken a side in this war. The 'west' is now imposing sanctions against Belarus which will inevitably have negative consequences for ALL people in that country. If ProtonMail does not clean up its slate on this issue it must take responsibility for these.
This, from today's New York Times, includes several false claims:
The plane, a Ryanair Boeing 737 headed from Greece to Lithuania, was traveling through Belarusian airspace on Sunday when it was diverted and forced to land in Minsk, the capital, with an escort from a fighter jet. Roman Protasevich, a Belarusian opposition journalist who had been living in exile abroad, was detained along with his girlfriend after the plane landed.
Belarus’s president, Aleksandr G. Lukashenko, a brutal and eccentric strongman (sic), has claimed that he rerouted the plane because of an emailed bomb threat, not to seize Mr. Protasevich. But a Swiss email provider has said that the email cited by the Belarusian authorities was sent after the plane had already been diverted.
As we have showed previously the Ryanair plane was not "diverted and forced to land in Minsk". When the plane entered Belorussian airspace at about 12:30 local time (9:30 utc) it was informed by the Air Traffic Control (ATC) of Belarus that an email had been received by several airports that threatened to explode the plane over its destination in Vilnius. The ATC recommended to the pilot to land in Minsk. The pilot decided to do so by himself. The radio traffic between the pilot and the ATC has been published (scroll down) by the aviation authorities of Belarus. It is undisputed.
The NYT claims, relying of partial information by ProtonMail, that "the email cited by the Belorussian authorities was sent after the plane had already been diverted." The claim is false. There were two emails with bomb threats. One was received before the Ryanair plane entered the airspace of Belarus, the other was received after the pilot had already made his decision to land in Minsk. ProtonMail has so far only confirmed that the second email was send to Minsk. It has rejected to make comments about the first bomb threat email sent through its service to Minsk.
Here is how we know about the two emails.
The narrative of the incident (scroll down for the English version) by the Belorussian authorities starts with this:
On May 23, 2021, a written message with the following content in English was sent to the e-mail of the National Airport Minsk from the e-mail address protonmail.com:
A translation of the Russian language version of that paragraph is a bit more specific:
On May 23, 2021, a written message with the following content was sent to the e-mail of the National Airport Minsk info@airport.by from the e-mail address protonmail.com in English:
The radio talk between ATC and the pilot of flight RYR 1TZ has additional information about the email:
ATC: RYR 1TZ
Pilot: The bomb....direct message, where did it come from? Where did you have information about it from?
ATC: RYR 1TZ standby please.
ATC: 09:33:42: RYR 1TZ
Pilot: Go ahead.
ATC: RYR 1TZ airport security stuff informed they received e-mail.
Pilot: Roger, Vilnius airport security stuff or from Greece?
ATC: RYR 1TZ this e-mail was shared to several airports.
At 9:33 utc the Belorussian ATC knew that the email had been received by several airports in the region. This must have been the first email in question and the recipient field must have show several airport related email addresses.
We know that one of the other recipients of the email received by Minsk airport was an airport organization in Vilnius, Lithuania.
The Dossier Center, a rather shady anti-Russian outfit in London financed by the exiled billionaire and company raider Mikhail Khodorkovsky, has published this misleading narrative about the Ryanair incident (machine translation, emph. added):
Swiss Hamas - Inconsistencies in the "terrorist" version of the Belarusian authorities
On May 26, during a speech in parliament, Alexander Lukashenko commented on the emergency landing in Minsk of a Ryanair airline, on board which was the former editor-in-chief of the Nexta Telegram channel Roman Protasevich. Lukashenka said that the message about the mining of the side was received by “Athens, Minsk and Vilnius at the same time”. After the Belarusian air traffic controllers passed the information about the bomb allegedly received from the special services to the Ryanair pilots, it was decided to land the plane in Minsk. To escort the board, a MiG-29 fighter of the Belarusian Air Force was raised.
The Dossier Center, together with The Daily Beast and Der Spiegel, managed to obtain and analyze a copy of an email sent by a “Hamas representative” to the Minsk airport. It follows from it that the Belarusian air traffic controllers informed the Ryanair pilots about the mining of the plane 27 minutes earlier than they themselves received the message about the bomb.
On May 23, at 12:25 pm Belarusian time, the administration of “Lithuanian Airports” received a letter with a threat of a bomb explosion on board the flight FR4978, sent from the address [email protected].
The highlighted sentence says that a threat email arrived in Lithuania at 12:25 pm (9:25 utc). This must have been the same email which the Belorussian ATC mentioned at 9:33 utc:
ATC: RYR 1TZ this e-mail was shared to several airports.
Then however the Dossier Center claim in the second paragraph above, that "the Belarusian air traffic controllers informed the Ryanair pilots about the mining of the plane 27 minutes earlier than they themselves received the message about the bomb", makes no sense.
But the Dossier Center does show an email with a bomb threat that was received at 12:56 (9:56 utc) after the pilot had already made the decision to land in Minsk.

The explanation that resolves the seemingly contradicting evidence is simple. There were two emails sent to the airports.
In fact on May 28 the Investigative Committee of Belarus, the country's prosecution service, published a note about the case (machine translation, emph. added):
It has already been established, to which we draw special attention, that there were several messages about the "mining" of the aircraft received through the Swiss anonymous mail service ProtonMail - at 12:25 and at 12:56. At the moment, the records of conversations with the pilots of the aircraft are being studied and analyzed in detail, and numerous other investigative actions are being carried out.
The Dossier Center however claims, without providing any evidence, that Minsk did not receive the first email (machine translation, emph. added):
At 12:30 the plane entered the airspace of Belarus. As follows from the transcript of the dispatchers' negotiations with the Ryanair pilots, at the same moment the Belarusian side informed the crew about the alleged explosion threat. At 12:33 pm, the controller informed the pilot that a letter with a message about the bomb had been sent to several airports at once. However, as the Dossier Center found out, at that time only Lithuanian Airports received a letter from the “terrorists”. The Greek Civil Aviation Authority said it had not received a bomb threat letter at the Athens airport.
At 12:47 the plane changed course and flew towards Minsk. The official statement of the Aviation Directorate of the Ministry of Transport of Belarus did not disclose details about the time of receipt of the email, but Dossier found out that a copy of the letter from user Ahmed Yurlanov came to the email of the National Airport of Minsk ([email protected]) at 12:57 pm Belarusian time - that is, almost half an hour after the transmission of the message about the possible mining of the side.
How the anti-Russian Dossier Center in London would even know when and what emails arrived or didn't arrive at Minsk airport is inexplicable.
The Daily Beast has cooperated with the Dossier Center in reporting the issue. Its piece, authored by Michael Weiss, a former research director of the neo-conservative Henry Jackson Society in London, does not resolve the issue:
The email was sent to Minsk’s National Airport’s general information account at 12:57 p.m. on May 23, 27 minutes after the plane first entered Belarusian airspace and 24 minutes after air traffic control in Minsk first informed the Ryanair pilot that an emailed bomb threat was “shared with several airports.”
But the Greek Civil Aviation Authority, which is responsible for the plane that took off from Athens, has publicly stated that it received no such warning at any point during FR4978’s journey. Lithuania did receive the email, but not Vilnius Airport, the intended destination; rather, the recipient was State Enterprise Lithuanian Airports, the state-run company that handles three different Lithuanian airports (Vilnius, Kaunas, and Palanga).
That someone in Greece did not receive the bomb threat email and who in Lithuania received the email or not does not tell us anything about the reception of the first email in Minsk. The whole writeup is a diversion from that critical point.
Here is where ProtonMail comes in.
ProtonMail was asked about the second email published by the Daily Beast and the Dossier Center. It responded with a statement to Reuters which then misleading headlined:
Bomb threat cited by Belarus was sent after plane was diverted - Swiss email provider
A bomb threat cited by Belarusian authorities as the reason for forcing a Ryanair jetliner carrying a dissident journalist to land in Minsk was sent after the plane was diverted, privacy-focused email provider Proton Technologies AG said on Thursday.
...
Proton declined to comment on specifics of the message but confirmed it was sent after the plane was diverted."We haven't seen credible evidence that the Belarusian claims are true," the Swiss company said in a statement. "We will support European authorities in their investigations upon receiving a legal request."
ProtonMail seems to have confirmed to Reuters that the second email, received in Minsk at 12:56 (9:56 utc), had been sent through its service.
ProtonMail however seems to not have been asked about the first email received in Minsk and Lithuania on May 23 at 12:25 (9:25 utc). Still Reuters attributes the false claim, that the bomb threat cited by Belarus was sent after the plane was diverted, directly to ProtonMail. Belarus cited the first email sent. ProtonMail only confirmed that the second email was sent. It should be in the interest of ProtonMail to clear up that issue.
Yesterday evening I asked ProtonMail to explicitly confirm that the first email was also sent to and received in Minsk. As it confirmed that the second email was sent it should have no problem with confirming the first one too. This unless it has left its claimed neutrality and is an active participant in the information war against Belarus.
Here is the full exchange:
Chahuapa @Chahuapa - 22:22 utc · May 26, 2021
Email can be easily spoofed (appear to come from some adres when it's not). I suggest anyone to stop using protonmail. It has been compromised.
ProtonMail @ProtonMail - 18:10 utc · May 27, 2021
Replying to @ChahuapaThe email leaked to the press was not obtained from us. Due to our encryption, we can't access/verify the message contents. However, we can see the sent time and can confirm it was after the plane was redirected.
Moon of Alabama @MoonofA - 19:12 utc · May 28, 2021
Replying to @ProtonMail and @ChahuapaThe Belarus prosecutor states that it received two ProtonMails - at 12:25 and at 12:56 (UTC+3). sk.gov.by/ru/news-usk-gm...
Dossier Center claims that Lithuanian airports received threat email at 12:25.
Can you please confirm that the first email at 12:25 was also sent to Minsk.
ProtonMail @ProtonMail - 19:54 utc · May 28, 2021
Replying to @MoonofA and @ChahuapaUnfortunately we can't comment on this as the first email is not public information yet. Only the Swiss authorities can make additional disclosures at this time.
Moon of Alabama @MoonofA - 20:07 utc · May 28, 2021
Replying to @ProtonMail and @ChahuapaI contacted you because I learned of the first email from:
a. Dossier Center
b. General Prosecutor of Belarus
Their claims of reception of the 9:25 utc email in Vilnius and Minsk are already public information.
You are only asked to confirm that both were sent at that time.
There was no further response from ProtonMail.
While ProtonMail seems to confirm the existence of the first email it is not willing to confirm that the first email was also received in Minsk.
This is not helpful. ProtonMail's confirmation to Reuters that the second email was received in Minsk has led to widely misleading headlines and numerous reports which, attributed to ProtonMail, falsely claim that Belarus recommended the plane to land in Minsk without having received a bomb threat to that plane.
ProtonMail could easily clean up the false reports by confirming in a public statement that there were two emails and that the first email at at 12:25 (9:25 utc) was also sent to and received in Minsk.
That ProtonMail refuses to do so demonstrates that it is a party in the information war against Belarus. Swiss Neutrality this is not.
But ProtonMail claims neutrality. It also claims that its encrypted email service is secure.
In light of the above ProtonMail's neutrality seems to be quite questionable. That lets me doubt that its service and products are as secure as it claims.
There have been other Swiss providers of encryption technology and services who had made false claims about their neutrality. Their claims about the security of the encryption services they provided turned out to be false.
Last year this led to headlines like these:
- CIA and German intelligence agency secretly owned Swiss encryption company used by 120 governments - Telegraph
- Swiss report reveals new details on CIA spying operation - MSN / Washington Post
- Report Claims CIA Controlled Second Swiss Encryption Firm - AFP / Barrons
It is easy for ProtonMail to reclaim Neutrality by publicly providing information that an email from the account shown in the above screenshot or any other ProtonMail account was sent to the info@airport.by address in Minsk on May 23 at 9:25 utc. As ProtonMail confirmed that the second email was sent and received it must have the metadata that allows it to issue a similar confirmation about the first mail.
An additional public explanation of the fact that there were two emails in question and that its previous statement to Reuters was only with regard to the second email would be very helpful.
We should also keep in mind that this is not a question of good versus bad but true or false. One may dislike the leadership of Belarus. But one also has to acknowledge, as even The Atlantic does, that the government of Belarus acted in full accordance with the relevant laws:
Ryanair’s CEO called the incident “state-sponsored hijacking.” It was not. Technically, you have to be on a plane to hijack it. But the Ryanair incident was nevertheless diabolical—and what makes it particularly diabolical is that Belarus may have managed to pull it off without violating its agreements under international law.
One should also consider that the only casualty in this incident is an openly neo-nazi regime change activist who is financed by 'western' governments.
If ProtonMail wants to take that side it is free to do so. But it can not claim neutrality, and a secure service, while doing so.
Should ProtonMail change its mind and issue a clarifying statement on the issue I will update this post accordingly.
---
Previous Moon of Alabama post on the Ryanair incident in Belarus:
- Lukashenko's Revenge (Served Cold) - May 24 2021
- Roman Protasevich - Arrested In Belarus - Is A Western Government Financed Neo-Nazi - May 26 2021
- By The Book - What Really Happened With The Ryanair Flight In Belarus - May 27 2021
- Ryanair Incident - Email Warning Received Before Plane Entered Belorussian Airspace - May 28 2021
Posted by b on May 29, 2021 at 14:46 UTC | Permalink
And here's Part 2 of this drama, filed by MoA on May 30, 2021:
'Like An Amoral Infant' - How ProtonMail Contributes To False Media Claims About Belarus
ProtonMail, an encrypted end-to-end email provider in Switzerland which promises 'Swiss Privacy Data Security and Neutrality', has been busted for making false claims about bomb threat emails which were sent through its service to Minsk airport in Belarus as well as to airport authorities in other countries.
The despicable behavior of ProtonMail has led to false headlines like the one by UPI depicted below.

ProtonMail may or may not have made that quite explicit headline claim. It is however 100% false. Belarus received a legit bomb threat against a Ryanair flight via an email sent through the ProtonMail mail servers. After receiving the email it contacted the plane in question and recommended to the pilot to divert the plane to Minsk. The pilot voluntarily followed that advice.
ProtonMail has made no effort to correct the false impression and false headlines its statement has caused. It has instead obfuscated the issue as much as it could. That is neither neutral nor fair behavior but partisan lying in an information war waged by 'western' regime changers against the people of Belarus.
Due to the malign behavior of ProtonMail new sanctions against Belarus, which will directly or indirectly hurt every Belorussian citizen, were introduced by the United States, the EU and other countries.
Moon of Alabama has detailed the publicly available evidence of the case and has called on ProtonMail to correct the record. ProtonMail responded and communicated with me via Twitter. In its communication with me ProtonMail indirectly admitted that the above headline is wrong. The complete exchange is of public interest and therefore copied below.
How did this happen?
On May 23 at 9:25 utc some yet unknown person used a ProtonMail email account to send a bomb threat against Ryanair flight 4978 witch at that time was in the air flying from Greece to Vilnius, Lithuania.
The email was directly addressed in the "Send to:" field to the Lithuanian administration responsible for Lithuanian airports. The airport of Minsk, Belarus, with the email address info@airport.by, was copied in the "CC to:" 'Carbon copy' field of the very same email.
In communication with me ProtonMail tried to claim that this meant that Minsk was not directly addressed in that email. That is nonsense. Any email server will handled email addresses in the "Send To:", "Carbon Copy (CC) to:" and "Blind Carbon Copy (BCC) to:" fields equally in that it will resolve the IP-address of the appropriate server responsible for receiving emails to that email-address. It will then open a session with it that server and deliver the mail. It makes no difference for the receiving side in which "To:" field of the sent email it was mentioned. It will get a full copy of the email.
Minsk received the first email at 9:25 utc. At 9:30 utc Ryanair flight 4978 entered Belorussian airspace. It was immediately contacted by the Belorussian Air Traffic Control (ATC) and made aware of the bomb threat against the plane. The complete English language radio exchange between the Ryanair pilot, call sign RYR 1TZ, and the ATC as well as a narrative of what had happened was published by the Belorussian air traffic authorities (scroll down for the English version and the radio transcript).
The pilot then asked where the bomb threat had been coming from (emph. added):
ATC: RYR 1TZ
Pilot: The bomb....direct message, where did it come from? Where did you have information about it from?
ATC: RYR 1TZ standby please.
ATC: 09:33:42: RYR 1TZ
Pilot: Go ahead.
ATC: RYR 1TZ airport security stuff informed they received e-mail.
Pilot: Roger, Vilnius airport security stuff or from Greece?
ATC: RYR 1TZ this e-mail was shared to several airports.
At 9:33 utc (12:33 local time) the air traffic controller communicated that Minsk received the warning in an email that had been addressed to multiple entities.
This directly contradicts the above UPI headline which was based on a misleading statement ProtonMail had made towards news agencies.
The Ryanair pilot was warned of the bomb threat at 9:30 utc. He/she took until 9:47 utc to decide on the issue to then declare MAYDAY. Only several minutes later did the pilot changed the plane's course towards Minsk.
A second ProtonMail email with the bomb threat was received at Minsk airport at 9:56 utc (12:56 local time). The sender of the second email, which was addressed to info@airport.by in the "To:" field, might have watched the plane's course live on Flight Aware and likely prepared and sent the second email when the plane, as visible in the flightpath, seemed to not react to the first threat.

The pilots decided to go to Minsk because the risk of a potential bomb going off over Vilnius, as announced in the email, was high. The Belorussian authorities have handled the case by the book. They scrambled a fighter jet to watch over the plane as is usual with any plane that gets threatened or hijacked. The Ryanair pilot was left unaware of this.
On May 28 the Investigative Committee of Belarus, the country's prosecution service, published a note about the case (machine translation, emph. added):
It has already been established, to which we draw special attention, that there were several messages about the "mining" of the aircraft received through the Swiss anonymous mail service ProtonMail - at 12:25 and at 12:56. At the moment, the records of conversations with the pilots of the aircraft are being studied and analyzed in detail, and numerous other investigative actions are being carried out.
On May 26 the Dossier Center, a rather shady anti-Russian outfit in London financed by the exiled billionaire and company raider Mikhail Khodorkovsky, published a misleading narrative about the Ryanair incident. It produced a screenshot of the second email that had arrived at Minsk airport and falsely claimed that Belarus receive a bomb threat email only at 9:56 utc. The Daily Beast, which collaborated with the Dossier Center, headlined:
‘Bomb Threat' That Justified Belarus Hijacking Came 24 Minutes After
An exclusively obtained record shows that the Ryanair ‘Hamas bomb' email—which the Belarus president said prompted the jet landing—was sent after the crew was told of a ‘threat.'
The claim was false. Minsk airport, with the email address info@airport.by, had been CCed, 'Carbon Copied', in the 9:25 utc email sent "To:" Lithuanian authorities. Minsk airport was directly addressed in the second email of which the Dossier Center and the Daily Beast, by unknown means, acquired the screenshot they published.
News agencies then contacted ProtonMail and asked about the validity of the 9:56 utc email the Dossier Center had published. ProtonMail stated that the 9:56 utc email had been sent to Minsk airport. It did not mention that the 9:25 utc bomb threat email was also sent to Minsk airport. This obfuscation of the issue, and ProtonMail's unwillingness to correct the record, directly led to the false headlines and to sanctions against Belarus.
You can check the validity of the above narrative from my recent communication with ProtonMail, published for your amusement below. Earlier communication with ProtonMail was published in my previous post on the issue.
At some point the @ProtonMail account on Twitter requested to move the communication from the public realm to Direct Messaging (DM) mode. I followed up on that request. I was never asked to nor did I promise to keep the direct messaging exchange with @ProtonMail private. I believe that publishing its content is of public interest.
Here is a screenshot of the most relevant part.
And here is the whole rest of it, typos included:
Moon of Alabama @MoonofA - 14:51 utc · May 29, 2021
New on MoA:
How @ProtonMail Lost The Public Trust It Needs To Do Business
moonofalabama.org/2021/05/how-pr...
#Belarus
ProtonMail @ProtonMail - 15:07 utc · May 29, 2021
Replying to @MoonofA
Just to reiterate, it is not that we don't want to comment on the first email. Rather, our current privacy policy does not let us comment as the first email is not yet in the public domain. We do expect government authorities to disclose it eventually however.
Moon of Alabama @MoonofA - 15:12 utc · May 29, 2021
Replying to @ProtonMail
Knowledge of the first email is in the public domain - see my blogpost.
You can comment on the metadata of that first email just as you did comment on the metadata of the second email.
Media attribute a false claim to your company. It should by your interest to clean that up.
Moon of Alabama @MoonofA - 15:16 utc · May 29, 2021
Replying to @MoonofA and @ProtonMail
Any delay in clearing up this issue will create more damage and hurt people.
That on your conscience. But then don't claim to be neutral and secure.
ProtonMail @ProtonMail- 15:16 utc · May 29, 2021
Replying to @MoonofA
Then you would also be aware that the Lithuanian government did not contact Belarus, which raises the question of how did Belarus know about the first email.
Moon of Alabama @MoonofA - 15:17 utc · May 29, 2021
Replying to @ProtonMail
Because Belarus also received the first email. It states so in several documents.
It is on you to confirm that.
ProtonMail @ProtonMail - 15:21 utc · May 29, 2021
Replying to @MoonofA
Actually, if you double check the public reporting on the issue, sources are clear in stating that "only Lithuanian Airports received a letter".
Moon of Alabama @MoonofA - 15:24 utc · May 29, 2021
Replying to @ProtonMail
Dossier Center makes that claim but provides zero evidence for it. How would it know unless you checked your systems and told them?
Moon of Alabama @MoonofA - 15:26 utc · May 29, 2021
Replying to @MoonofA and @ProtonMail
BTW - I just wrote a 2600 word blogpost on the issue.
You may want to read that.
Some 50,000 other people will do so.
ProtonMail @ProtonMail - 15:27 utc · May 29, 2021
Replying to @MoonofA
We have never had contact with Dossier Center. Any information, would have been obtained from Lithuanian authorities with access to the email.
ProtonMail @ProtonMail - 15:30 utc · May 29, 2021
Replying to @ProtonMail and @MoonofA
As we have already reiterated, none of the emails which have been cited in any of the reporting, are sourced from us, because we cannot read/access emails due to our encryption, which can be verified in our publicly audited source code.
ProtonMail @ProtonMail - 15:44 utc · May 29, 2021
Replying to @ProtonMail and @MoonofA
Lastly, we can't comment on non-public information found in external reporting. Your question should be directed to the source of this information, the dossier center, and not to Proton.
Keith Granger @regnarGhtieK - 18:11 utc · May 29, 2021
Replying to @ProtonMail and @MoonofA
Wow, Proton, there is no good reason for you to not tell the world the timing of the first email & whether it went to Belarus or not
You've already said enough to cause harm & made yourselves look partisan
Do you have no shame - as of right now you look like an amoral infant.
ProtonMail @ProtonMail - 18:16 utc · May 29, 2021
Replying to @regnarGhtieK and @MoonofA
Commenting on non-public information related to an on-going Swiss govt investigation is generally not permissible. @MoonofA can DM us for clarification.
At 18:18 utc yesterday I followed up on @ProtonMail's suggestion to move into Direct Messaging (DM) mode. Tweets exchanged in that mode are not directly linkable. I copy/pasted the exchange below. For clarity I have marked tweets from my @MoonofA account with a preceding "M:". Tweets by the @ProtonMail account are preceded by "P:". I also provide screenshots of the complete communication (1, 2, 3, 4). The screenshots were made today, May 30. The time marks displayed in the exchange are UTC+2.
ProtonMail @ProtonMail
Incoming envelope Secure email that respects your privacy, brought to you by CERN and MIT scientists. Creators of @ProtonVPN & @ProtonCalendar | Maintainers of @openpgpjs
321 Following 218.6K Followers
Joined October 2013M:
So now you claim that there is a Swiss government investigation.
Wondering why there would by one?
Yesterday, 8:18 PMP:
There is an investigation ongoing, and as disclosed in our statement yesterday we have received legally binding requests from the swiss government. It seems you are determined to push the belarusian narrative. if you were to receive confirmation that there was no first email sent to minsk, would you actually change your story?
ProtonMail
Yesterday, 8:22 PMM:
I do not push anyone's narrative but analyze facts and point out were I see mismatches in the various claims.
If you would publicly(!) state that there was no email sent from any ProtonMail account to info@airport.by on May 23 at or about 9:25 utc I would publicly accuse the government of Belarus of publishing misleading information. I would also publicly demand an explanation from it.
Yesterday, 8:33 PMP:
we are not permitted to comment on specifics, but we can say that the reporting by dossier.center is more correct than the belarussian version, which by the way, does not explicitly say that the first email was sent to minsk. all they did was repeat the claim that there was a first email, without clarifying where it was sent.
in other words, the conclusion you have drawn in your blog post is incorrect and we hope you will correct it.
ProtonMail
Yesterday, 8:41 PMM:
That is, again, a very mealymouthed ("more correct") and unproven claim by you.
You are insinuating that Minsk got the email from elsewhere, not from ProtonMail.
Maybe by snooping on Lithuanian accounts or by being copied on emails sent from a Lithuania administrative account to its airports.
Knowing the current hostile relations between Lithuania and Belarus and the Belarus statement on the issue we can exlude the second alternative.
We are told by Dossier Center that the 9:25 utc email was sent to one Lithuanian administrative account, not directly to its airports. The ATC in Belarus tells the pilot at 9:33 utc that the email "was shared to several airports".
Belarus prosecutor also claims that the email arrived in Minsk from ProtonMail at the very same minute that Dossier Center says it arrived in Lithuania.
The facts and timeline I know of are inconsistent with a snooping operation and with a sharing of the email by Lithuania.
My conclusion are unchanged.
Yesterday, 9:10 PMP:
Only one email went to belarus, and it was the one that dossier center published, which is in public domain.
ProtonMail
Yesterday, 9:12 PMM:
Interesting claim, made privately in a DM, but I fail to accept that as it is not a 'public domain' fact.
As I said: "If you would publicly(!) state that there was no email sent from any ProtonMail account to info@airport.by on May 23 at or about 9:25 utc ..." I will change my conclusions (and blog post).
(PS: It is nearing bedtime here and social responsibilities demand me to sign off for today.)
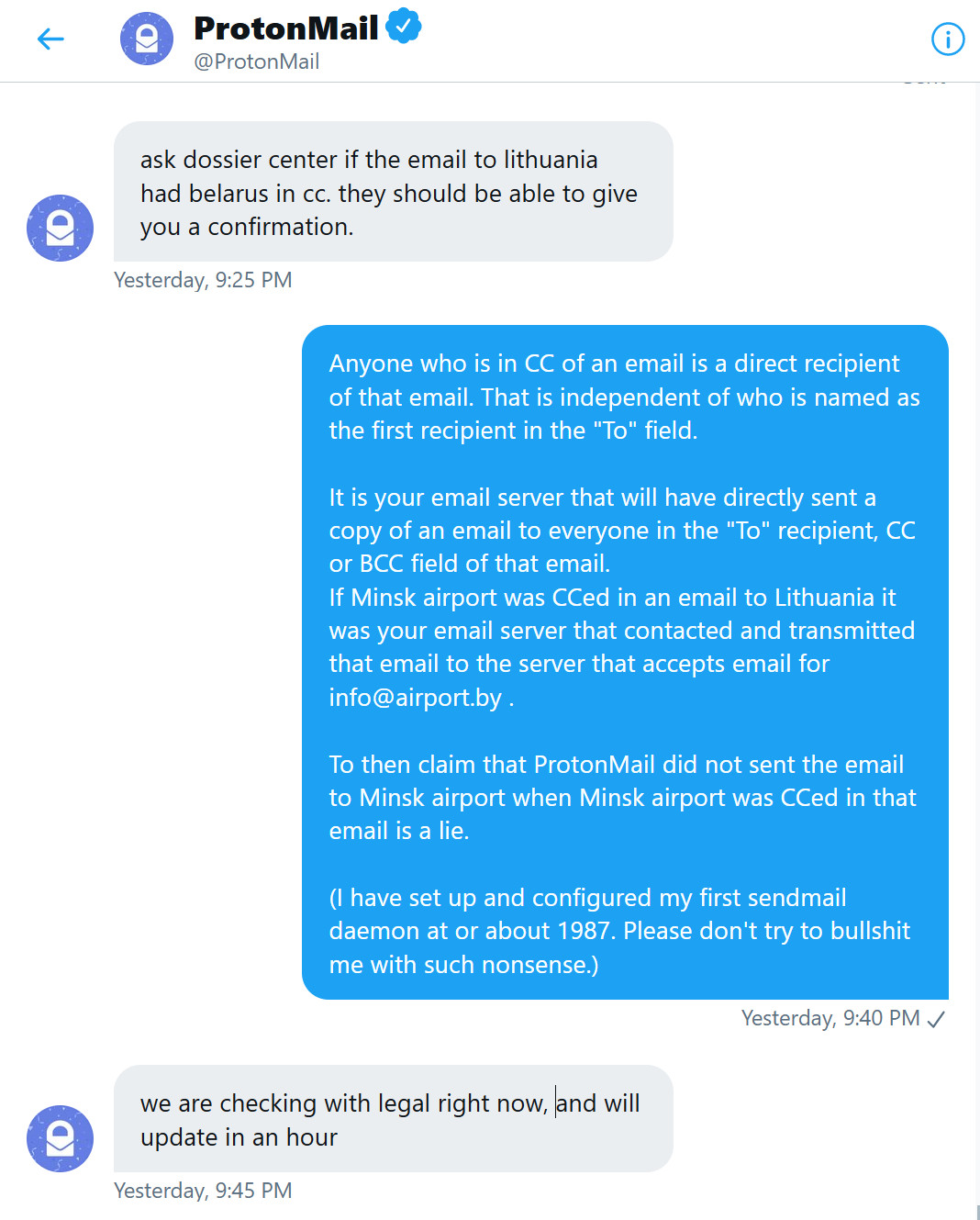
Yesterday, 9:21 PMP:
ask dossier center if the email to lithuania had belarus in cc. they should be able to give you a confirmation.
ProtonMail
Yesterday, 9:25 PMM:
Anyone who is in CC of an email is a direct recipient of that email. That is independent of who is named as the first recipient in the "To" field.
It is your email server that will have directly sent a copy of an email to everyone in the "To" recipient, CC or BCC field of that email.
If Minsk airport was CCed in an email to Lithuania it was your email server that contacted and transmitted that email to the server that accepts email for info@airport.by .
To then claim that ProtonMail did not sent the email to Minsk airport when Minsk airport was CCed in that email is a lie.
(I have set up and configured my first sendmail daemon at or about 1987. Please don't try to bullshit me with such nonsense.)
Yesterday, 9:40 PMP:
we are checking with legal right now, and will update in an hour
ProtonMail
Yesterday, 9:45 PMP:
but as we mentioned already, Only one email went to belarus, and it was the one that dossier center published, which is in public domain.
ProtonMail
Yesterday, 9:46 PMP:
Clarification regarding ProtonMail, Belarus, and Ryanair flight 4978
protonmail.com
we are going to update our statement here (http://protonmail.com/blog/belarus-ryanair) later tonight. will you be updating your blog to report the truth?
ProtonMail
Yesterday, 10:12 PM
The 'updated' statement that ProtonMail published is again a mealymouthed obfuscation which in no way clarifies the issue. It says:
The only email sent to Belarus was published by dossier.center to demonstrate that the “bomb threat” was sent after Ryanair flight 4978 was redirected.
That statement is however in contradiction to the public ProtonMail tweet at 15:07 utc · May 29, 2021:
... it is not that we don't want to comment on the first email. Rather, our current privacy policy does not let us comment as the first email is not yet in the public domain ...
It is also contradicted by the Belorussian prosecutor who clearly states:
... there were several messages [...] received through the Swiss anonymous mail service ProtonMail - at 12:25 and at 12:56 ...
It seems to be clear from the above communication and the publicly known facts that Minsk airport was CCed in the first email on May 23 9:25 utc which was primarily addressed to the Lithuanian airport authority. While Minsk was CCed in the 9:25 utc email it was primarily addressed in the second email received at 9:56 utc.
ProtonMail tries to differentiate between recipients of an email which are primarily addressed in the "To:" field and those which are copied in the "CC:" 'carbon copy' field. That is legally gibberish and technically nonsense. The sending email server, here ProtonMail's, will have handled all those addresses equally.
ProtonMail has the metadata which shows that info@airport.by in Minsk was carbon copied on the 9:25 utc email. It has stated to news agencies that (only) the second email was directly addressed to Minsk airport. This led to the false or misleading headlines and reporting as well as to sanctions against the people of Belarus. ProtonMail seems unwilling to publicly clarify the issue. It is not 'neutral' but is taking part in an information war waged by the 'west' against the people of Belarus.
Now ask yourself if you can trust ProtonMail with the handling of any of your 'encrypted' emails.
PS: We do not know who sent the bomb threat emails and for what purpose. Some will speculate that some Belorussian authority did so. Others will speculate that the 'regime change' opposition did it so to hurt Belarus. There is no public evidence to support either claim.
We do know that Belarus, after it received the 9:25 utc bomb threat email, handled the case by the book and within the realms of international law. After being informed of the threat the Ryanair pilot decided to divert the plane to Minsk where it was searched for a bomb. When none was found the crew and all passengers, except for two for whom there were outstanding arrest warrants and three who had had Minsk as their final flight destination, reentered the plane and flew to Vilnius.
I do not support the government of Belarus. But I also see no reason to criticize its behavior in this case. There is reason though to criticize the misreporting of the incident in 'western' media and to condemn ProtonMail's obfuscation which. at a minimum, contributes to that.
---
Previous Moon of Alabama post on the Ryanair incident in Belarus:
- Lukashenko's Revenge (Served Cold) - May 24 2021
- Roman Protasevich - Arrested In Belarus - Is A Western Government Financed Neo-Nazi - May 26 2021
- By The Book - What Really Happened With The Ryanair Flight In Belarus - May 27 2021
- Ryanair Incident - Email Warning Received Before Plane Entered Belorussian Airspace - May 28 2021
- How ProtonMail Lost The Public Trust It Needs To Do Business - May 29 2021
Posted by b on May 30, 2021 at 11:09 UTC | Permalink
Let this be a lesson to those reading (eg) articles in the Guardian and other propaganda-porn and jumping to the conclusion that promoted security solutions are "independent", "end-to-end encryption", "save no user data", "safe" ... etc. They are usually honeypots - whether Tor, Signal, search engines, proxy servers, VPN's, ... or whatever.
Posted by: BM | May 30 2021 11:32 utc | 2
Security on the internet is not to be had. The internet is not a safe place.
It is the land of bullshit and deception and grift.
The sooner everybody figures that out, the better off.
The old helpful informative internet was killed long ago by greed.
Posted by: Bemildred | May 30 2021 11:39 utc | 3
The replies of protonmail to your question are indeed infantile and stupid.
Posted by: svaya | May 30 2021 11:41 utc | 4
If Protonmail knows about the email metadata such as To: and CC: and BCC: that means it's not a pure anonymous mail service. That level of detail would allow any security agency to do 90% of the work in tracing communications between individuals.
So the question is, who is protonmail selling the metadata to?
Posted by: Jezza | May 30 2021 11:53 utc | 5
Well done b
Why doesn't anyone talk to Ryanair or to the pilot? Surely he will know, the plane recorder should also have the information, the Swiss outfit should be ignored as unreliable.
The Western MSM poodle will of course ignore the truth, they cannot do anything else.
Posted by: Baron | May 30 2021 11:55 utc | 6
Thanks b
Posted by: Baron | May 30 2021 11:55 utc | 6
Yes on lame stream press.
Posted by: jo6pac | May 30 2021 11:59 utc | 7
To be fair to protonmail, their position is that they have no way of knowing what was contained in any email so they have no way of knowing how many emails containing bomb threats there are or when they were sent or to whom they were sent.
Apparently someone who had access to the second email to Belarus released it and protonmail cannot confirm the contents of that email but can confirm the time stamp matches their records.
The question is why has the first email (if it exists) not been made public?
If the first email was published and widely circulated then protonmail could be able to verify (or deny) the recipient and timestamp in the email header. Until that happens protonmail's privacy policy prevents them from commenting.
Posted by: jinn | May 30 2021 12:01 utc | 8
Now does Protonmail work?
Only email sent from one Protonmail address to another can be end-to-end encrypted. If the encrypted email is sent to a normal email address (like info@airport.by), then Protonmail must be able to decrypt it.
Does Protonmail keep copies of a user's sent emails, like Gmail does? If so, then it is false to claim Protonmail cannot access the content of the email.
How about multiple recipients? Would Protonmail send individual emails to each recipient, or would everyone receive the same email with the full list of recipients? For privacy reason, a sender might sometimes not want email recipients talking to each other. There is no reason to believe it happened in this case. Such obfuscation would destroy the credibility of the bomb threat.
***
Is the screenshot a forgery?
As Diagonal pointed out, there are hints at forgery in the screenshot.
I too believe the screenshot is a forgery. I have been trying to figure out what email program was used to display the email. To me it looks most like Gmail for some mobile device. But most of the screen is photoshop. The bomb threat text itself looks like copy-paste from some newspaper.
Another sign is the up-down arrow at the end of the To: line. In the default position it is down. Clicking it expands the header fields with the arrow left in the up position. In the screenshot the text is placed where the email headers should be.
The forger would however need to know the time of the second email. Khodorkovsky, or whoever might have forged it, could have received this information from the Vilnius airport. The original sender would also know the time, so they could have forged it to make it look like they were the receiver.
Posted by: Petri Krohn | May 30 2021 12:09 utc | 9
If you find the above useful, pass it on! Become an "influence multiplier"!
The battle against the Big Lie killing the world will not be won by you just reading this article. It will be won when you pass it on to at least 2 other people, requesting they do the same.
| Did you sign up yet for our FREE bulletin? It's super easy! Sign up to receive our FREE bulletin. Get TGP selections in your mailbox. No obligation of any kind. All addresses secure and never sold or commercialised. |
[premium_newsticker id="211406"]
The views expressed are solely those of the author and may or may not reflect those of The Greanville Post
YOU ARE FREE TO REPRODUCE THIS ARTICLE PROVIDED YOU GIVE PROPER CREDIT TO THE GREANVILLE POST
VIA A BACK LIVE LINK.





I hope Belarus will file court proceedings against Protonmail for damages. Also I hope Protonmail users will file court proceedings for deception, as the case proves that their claims to be neutral are false; elsewhere it has also been proven that their claims of end-to-end encryption are also false, and that Protonmail can evidently access content. It is obviously a CIA/NSA honeypot.
In fact, why not Belarus facilitate a class action by Protonmail users?
Posted by: BM | May 30 2021 11:27 utc | 1